

Do you own a blog on WordPress.com website? If so, then you should take extra care while signing into your WordPress account when connected to public Wi-Fi, because it can be hacked without your knowledge, even if you have enabled two-factor authentication.
Yan Zhu, a researcher at the Electronic Frontier Foundation (EFF) noticed that the blogs hosted on WordPress are sending user authentication cookies in plain text, rather than encrypting it. So, it can be easily hijacked by even a Script-Kiddie looking to steal information.
When WordPress users log into their account, WordPress.com servers set a web cookie with name “wordpress_logged_in” into the users’ browser, Yan Zhu explained in a blog post. He noticed that this authentication cookie being sent over clear HTTP, in a very insecure manner.
One can grab HTTP cookies from the same Wi-Fi Network by using some specialized tools, such as Firesheep, a networking sniffing tool. The cookie can then be added to any other web browser to gain unauthorizedaccess to the victim’s WordPress account and in this way a WordPress.com account could be easily compromised.
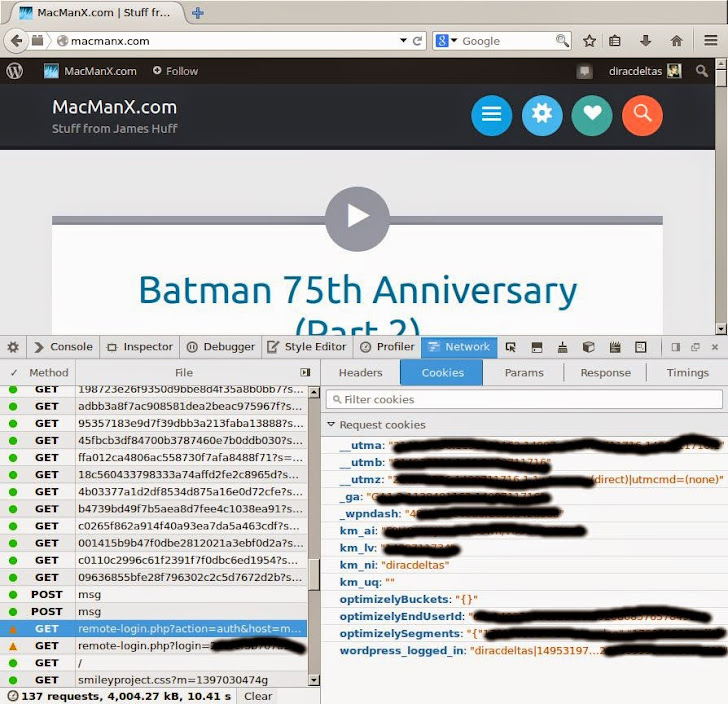
Using stolen cookies, an attacker can get access to the victim’s WordPress account automatically without entering any credentials and fortunately the vulnerability does not allow hijackers to change account passwords, but who cares? as the affected users would have no knowledge that their wordpress account has been hijacked.
Using this technique, one can also see blog statistics, can post and edit articles on the hijacked WordPress blog and same account also allows the attacker to comment on other WordPress blogs from the victim’s profile. Sounds Horrible! Isn’t it?
But, an attacker couldn’t do some blog administrator tasks that required logging in again with the username/password, but still, not bad for a single cookie.” she explained.She recommends that WordPress ‘should set the “secure” flag on sensitive cookies so that they’re never sent in plaintext.
The Good news is that, if you own a self-hosted WordPress website with full HTTPS support, then your blog is not vulnerable to cookies reuse flaw. Recently, similar Cookies reuse vulnerability was discovered by ‘The Hacker News’ team on eBay website, that could allow an attacker to hijack eBay accounts without knowing the victims’ actual credentials.
Read the full story on thehackernews.com