If you think hackers get a bad rap, think about this……
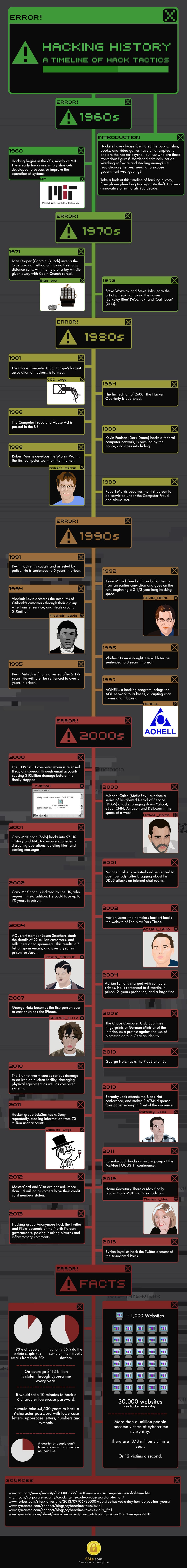
The word “hacking” has become synonymous with ill doings and the amount of affected people might be the reason for that. The meanings of hacking are many and most are intended to describe the act of engaging in activities (such as programming or other media) in a spirit of playfulness and exploration. But, the destructive intentions of some hackers have turned this word into something bad. For a better understanding, let’s have a look at the hacking history timeline.
It interesting to see that the hacking history timeline really began back in the 1960s as shortcuts developed to bypass or improve the operation of systems. In our concerned eyes today even this sounds malicious to a lot of people, but back then it was merely intended to quicker evaluate and improve faulty systems that had to be optimized. As we know, that’s not exactly what the word “hacker” stands for today. The word is, however, misused in the broad perspective and should really be replaced by the word “cracking,” which is the correct word used in the hacker subcultures around the world. It basically means to force or bypass security systems that are in place to protect the integrity and information stored within the systems attacked.
This hacking history timeline is a great overview of the world’s most notorious breaches and could serve as a reminder how important it is for all of us to stay up to date with our security updates and passwords in order for our personal information to stay safe.
With mobile devices soon to be the most used and accessible “computer” it’s somewhat worrying to see that we currently care more about the security of our PCs than we care about the security of our mobile devices. After having a look at this hacking history timeline, we are sure you’re going to change your mind about that. 90% of people delete suspicious emails from their PCs but only 56% do the same on their mobile devices. Why is that? It could be contributed to the fact that we trust developers and manufacturers too much these days when it comes to our mobile devices. Even though initially we didn’t see many maliciously intended break-ins into our mobile devices but that has dramatically changed in the past few years of the hacking history timeline.
Read the full story on bitrebels.com