

We offer a wide range of security services offerings, all designed to help improve and maintain your overall security posture.
Whether your goal is to comply with regulatory requirements, test your system for vulnerabilities or improve your overall security posture, we can tailor an offering to meet your needs.
At TBG Security we don’t believe one size fits all so what may fit for a comparable organization may not meet your security needs today. We strive to deliver our services with flawless execution in the most professional manner.
Contact Us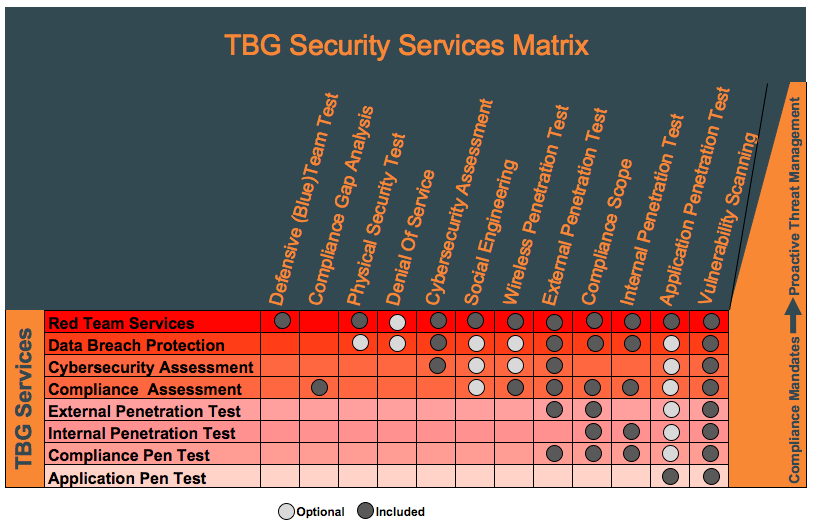
This TBG Security Services Matrix, below, shows you exactly how we bundle our services.
We know that one size most definitely does not fit all, so we provide a number of offerings focusing on specific IT security objectives. We can also customize our services to meet your specific needs.
Below the matrix, you get an overview of each individual service and a direct link to more information.
