
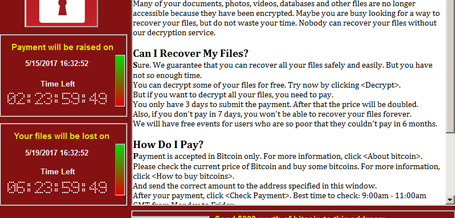
WannaCrypt, aka WanaCrypt0r 2.0, WannaCry and WCry, is a new ransomware that hit over 74 countries in the last 24 hours, which spreads like a worm by leveraging a Windows vulnerability (MS17-010) that has been previously fixed by Microsoft in March of this year. WannaCry is a form of “ransomware” that locks up the files on your computer and encrypts them in a way that makes them unavailable to you anymore.
The express train speed with which this has spread indicates users have not yet installed the security patch released in March (MS17-010) or they are still running an unsupported version of Windows for which Microsoft is no longer providing any any security update. Once it infects your machine, WannaCry demands payment in Bitcoin, gives instructions on how to buy it, and provides a Bitcoin address to send it to. What makes this different from previous ransomware is that its designers have supercharged it by using tools leaked by the super hackers at US National Security Agency (NSA).
Here are some quick links to much more technical details the team at The Register have gathered:
Any ransomware infection typically leverages spam, phishing or some form of social engineering as its primary attack vector, fooling users into downloading and executing a malicious file attachment.
FoxIT researchers have discovered that WannaCry is also leveraging a social engineering variant of the ransomware that is initially distributed via an email containing a link or a PDF file with payload, which when clicked, installs WannaCry on the targeted system. WannaCry then attempts to leverage its newfound foothold to disseminate copies of itself through the infected host’s network.
The Hacker News is reporting that once executed, the self-spreading WannaCry ransomware does not infect the targeted computers immediately, as malware reverse engineers found that the dropper first attempots to connect the following domain, which was initially unregistered:
hxxp://www[.]iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com
If the connection to the above-mentioned unregistered domain fails (which it obviously should), the dropper proceeds to infect the system with the ransomware that would start encrypting files. But if the connection is successful, the dropper does not infect the system with the WannaCry ransomware module.
As of now, over 100 countries have been infected:
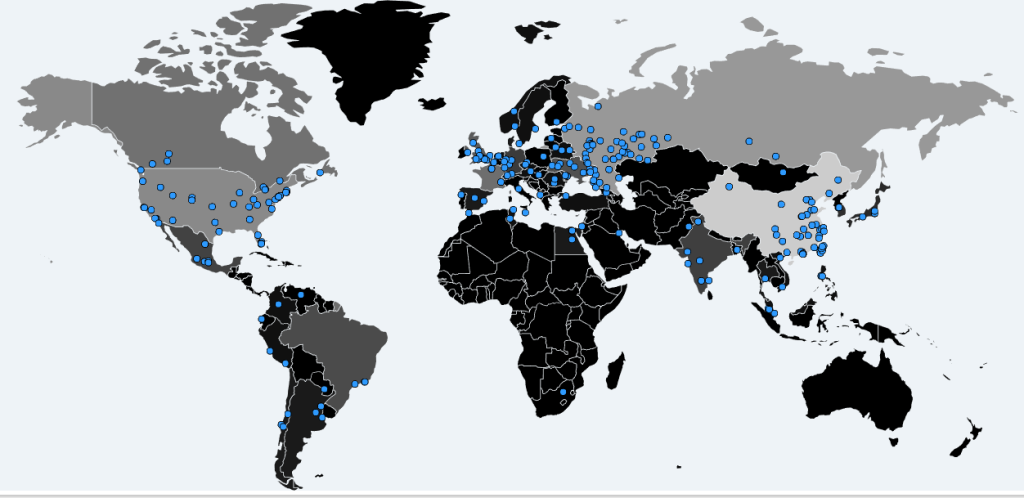
Source: Malwaretech
Patching makes Perfect. First, if you have not already patched your Windows machines and servers against the Microsoft vulnerability exploit (MS17-010), do it right now. Microsoft’s Windows Defender AV detects and removes this threat. as well.
To reduce the possibility of becoming infected with ANY ransomware infection, do not open uninvited emails, emails from people or businesses you do not recognize and NEVER click on any attachments unless you know what you are opening. And as a best practice you should always backup your files to some type of external device that is not connected to your PC or your network.
If you don’t have an AntiVirus software package running on your PC (what are you thinking) then install one ASAP and keep the definitions up to date. Most, if not all Av packages will automatically update the virus definitions but it’s up to you to set up an effective scanning solution.