

We typically understand a ransomware attack to be a demand for payment in return for decrypting files. But evolution, even in malware, is inevitable. A fairly new disruptive cyber cell known as The Dark Overlord is relying on the threat of reputation damage to “encourage” its victims to pay up.
You might be thinking that reputation damage wouldn’t be enough to make your firm shake in its boots, but you’d be wrong. These Dark Overlord cyberbullies use nasty tactics to get a hefty Bitcoin payment.
To beat them, you need to understand how they operate.
What do we know about Dark Overlord?
Since summertime last year, The Dark Overlord have been digitally terrorizing companies and public institutions like hospitals and schools.
Their modus operandi is get into unauthorised networks, hunt down and steal sensitive files and private information, and then demand a payment for its return. Their attack style seems very targeted, and they use the information they’ve nabbed to both prove what they have and to threaten the victims.
This is somewhat different to typical ransomware where files are held hostage in the hope that the company does not maintain its back ups. Here they simply have the sensitive information in their possession. The threat is that it will be shared or sold it if the ransom isn’t paid on time. They also use the press to undermine any efforts on the part of the victim to keep the attack quiet.
Who have they attacked?
A few weeks ago, Dark Overlord successfully attacked Hollywood production studio Line 204, claiming to have obtained the addresses and phone numbers of celebrities. Line 204, whose sound stages have hosted the likes of Nicole Kidman, Britney Spears, Katie Holmes, Jennifer Lopez, Quentin Tarantino, Ridley Scott, says that it has called in the FBI.
Earlier last month, The Dark Overlord also successfully stole a database of plastic surgery patients from the UK’s London Bridge Plastic Surgery and Aesthetic Clinic, a clinic reportedly used by high-profile individuals, such as celebrities and royals. The hackers actually contacted The Daily Beast, saying that they had terabytes of data on the clinic’s customers. They threatened to release more data unless an undisclosed ransom is paid.
“There are some royal families in here,” the hackers said. “We’re going to pitch it all up for everyone to nab – the entire patient list, with corresponding photos. The world has never seen a medical dump of a plastic surgeon to such a degree.”
In previous campaigns, the cyber villains threatened violence against school districts, even intimidating parents by texting threatening messages to them using their kids’ cell numbers.
They then punished the schools for not paying up by dumping the stolen data on Pastebin. The now-deleted post included “student names, addresses and telephone numbers.” The Dark Overlord even posted on Twitter:
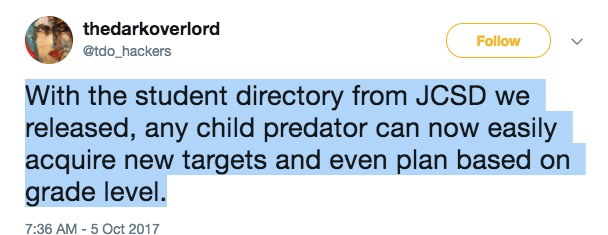
You can imagine the incredible pressure the schools were under. Parents would be all over this, like a swarm of angry bees, wanting to know how it happened, and how to stop it.
Do victims organizations just pay ransoms?
Yes, some people do, but the problem here is that there is no guarantee the attackers will return or delete the data. In fact, it is very unlikely they would actually fully delete the data that they’ve successfully stolen. With any ransom demand, once paid, what is to stop them coming after you at another time? After all, they’ve already established that you can be intimidated, and they still hold the sensitive information.
Paying means that that you are endorsing and encouraging the behaviour by providing an actual market for these ne’re-do-wells. If you find yourself a victim of this type of ransomware attack, you are strongly encouraged to contact the authorities and get them involved.
How NOT to be a victim
Well, the old ransomware trick of ensuring you have backups doesn’t cut it here. They don’t care whether you can still access the data. The fact that they have a copy of the data to do with what as they please is enough to severely disrupt normal operations.
The trick is to be a less attractive target than the average company out there. By making yourself a more difficult nut to crack, attack agents are likely to move on to an easier target.
Here is TBG Security advice.
How TBG Security can help
TBG Security are experts at hardening IT systems to thwart both opportunistic and targeted attacks, as well as safeguarding sensitive data. They use the latest hacker tools and approaches to uncover vulnerabilities, and prioritise them according to risk exposure and threats to business continuity.
Get in touch to see how they can help your organization be as unattractive as possible to nasty cyber agents hunting down their next victims.