

If you’re storing personal information in a cloud service like DropBox or Box, even Google Drive we have to ask, what are you thinking? If you somehow have been convinced that these are secure platforms for sharing personal information you might think again after reading Graham Cluley’s piece below.
If you are using file-sharing systems like Dropbox and Box without proper care and attention, there is a risk that you could be unwittingly leaking your most private, personal information to others.
And the risk isn’t theoretical.It’s happening right now – exposing tax returns, financial records, mortgage applications and business plans.
Enterprise file-sharing company Intralinks discovered the serious security issue by accident, when examining its Google Analytics web traffic data and Google Adwords reports.
Like many other companies, Intralinks has webpages, content and – yes, they admit it – Google Ads which are designed with the intention of appearing when users search for the names of their competitors.
Lots of companies do this. It’s the reason why if you Google a phrase like “dropbox secure file sharing” you’ll see ads and links not just for Dropbox, but for competitors too.
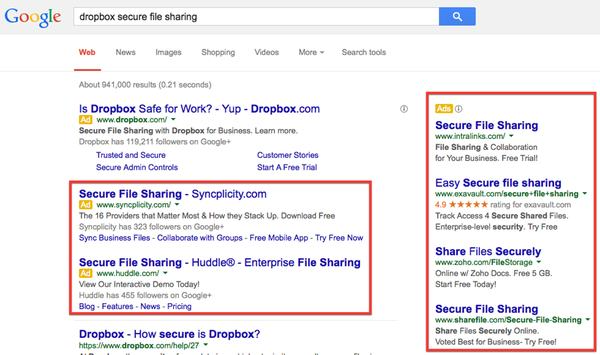
Similarly, if you Google “Intralinks file sharing” you’ll see ads for Dropbox and others.
No-one is saying that this is a bad thing – the sites concerned aren’t pretending to be something they’re not, and it’s just a healthy competitive marketplace at work, informing you of your choices as a consumer.
But, when Intralinks looked at the data from Google Adwords campaigns that mentioned its competitors Box.com and Dropbox, they found something which shocked them: the fully clickable URLs required to access documents stored on the services, including some containing clearly sensitive information.
For example, here is one person’s income tax return scooped up from Dropbox.(The image has been redacted below to preserve the individual’s anonymity.)
Read the full story on grahamcluley.com