Ah the necessary evil of passwords.
Those of us who have worked in organizations that require users to change passwords at set intervals know what I mean.
Typically every three to six months, users are requested to perform a password change – maybe in the form of an annoying pop-up alert. In some setups, the user is lock out of the system until a new memorable password (but one that follows the complex password creation guidelines) is set.
A commenter on Slashdot said his previous organisation demanded a password change every 45 days. Gulp.
Under that pressure, is it surprising that so many users forget their new passwords or resort to cobbling together poor passwords?
But, it’s no picnic for IT teams either. IT represents one of the most under-resourced, yet critical departments in many an organization. The regularly changing your password policy demands that IT manage this whole process, including when users forget their ‘memorable’ passwords. It takes time, effort and money to run this security policy.
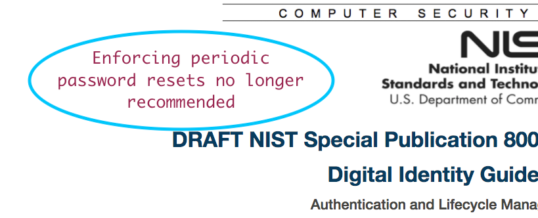
And part of the reason regular password reset have been enforced is because organizations like the United States National Institute for Standards and Technology (NIST) have advocated this approach….until last week.
New Password Guidelines from NIST
NIST released a new draft of its Digital Identity Guidelines: The Special Publication 800-63-3b. No longer does NIST recommend forced password changes or additional complexities when asking users to select a password.
In fact, they seem to prefer the term Memorized Secrets, over passwords:
“A Memorized Secret authenticator (commonly referred to as a password or, if numeric, a PIN) is a secret value that is intended to be chosen and memorable by the user. Memorized secrets need to be of sufficient complexity and secrecy that it would be impractical for an attacker to guess or otherwise discover the correct secret value.”
In fact, way back in 2009, NIST admitted that enforced password changes were a source of frustration to the user.
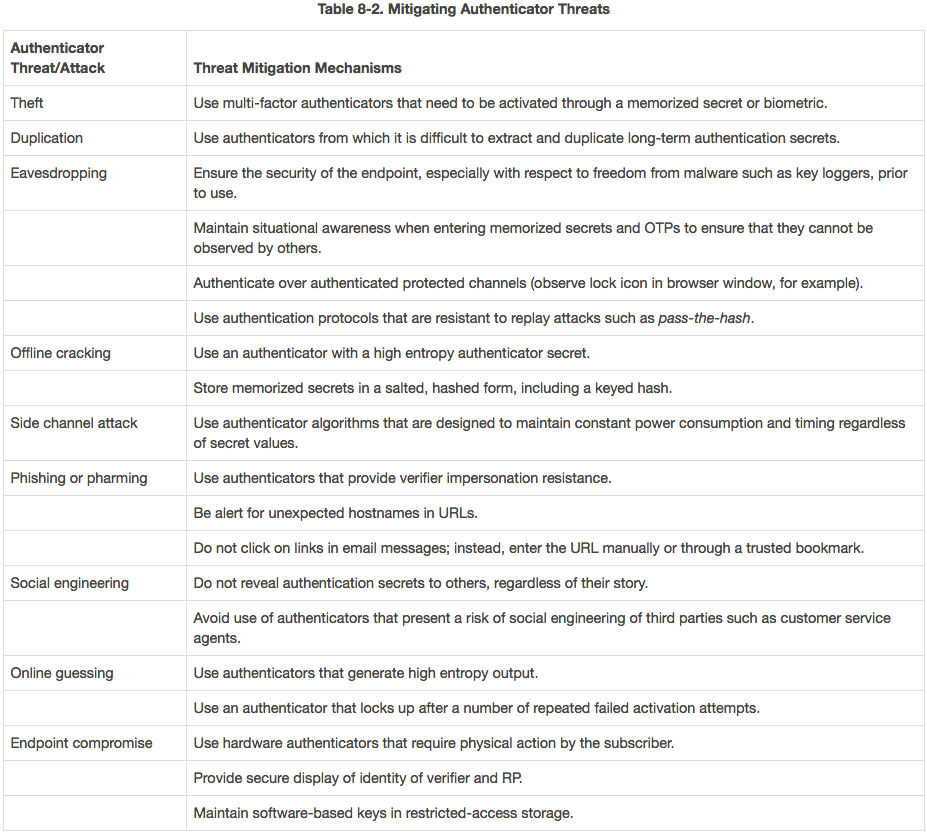
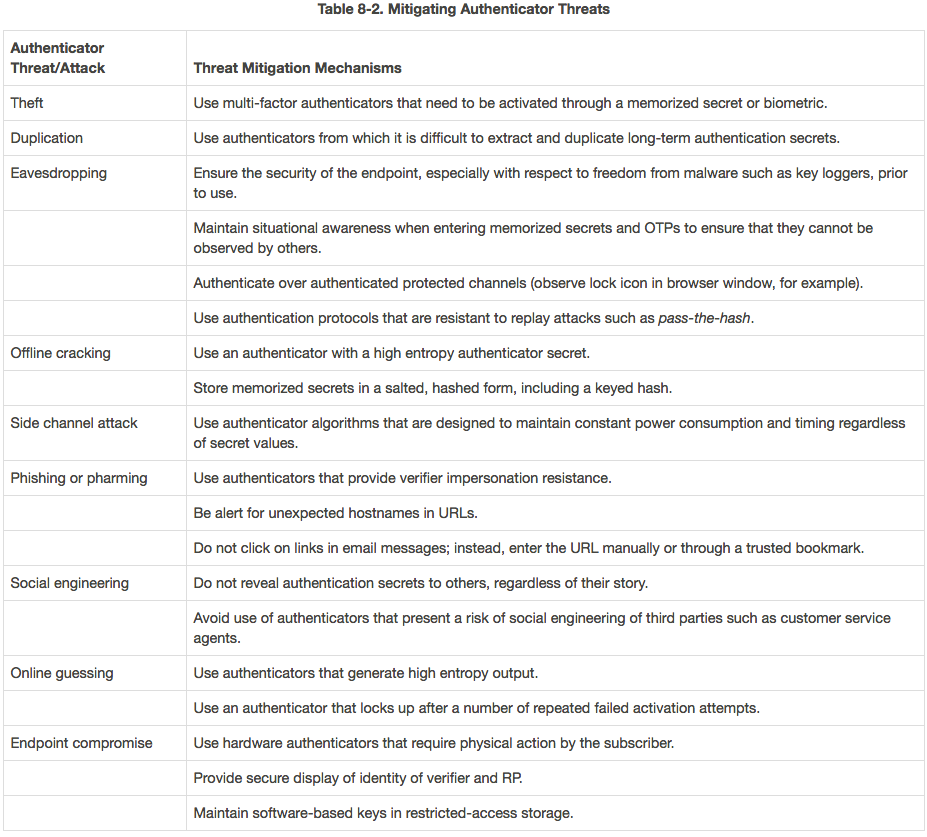
According to the NIST guidelines, the new draft rules on password policies include: