
Cyber criminals remain indifferent and insensitive to events showcased on the national stage, such as the bombings at the Boston marathon on April 15, 2013. Since the event, the Dell SecureWorks CTU(TM) research team has been monitoring the Waledac/Kelihos botnet, which has begun distributing spam claiming to provide information about the bombing (see Figure 1). The email messages contain a single malicious link and entice victims to click the link for more information.

Figure 1. Example of spam subject lines. (Source: https://www.malekal.com/)
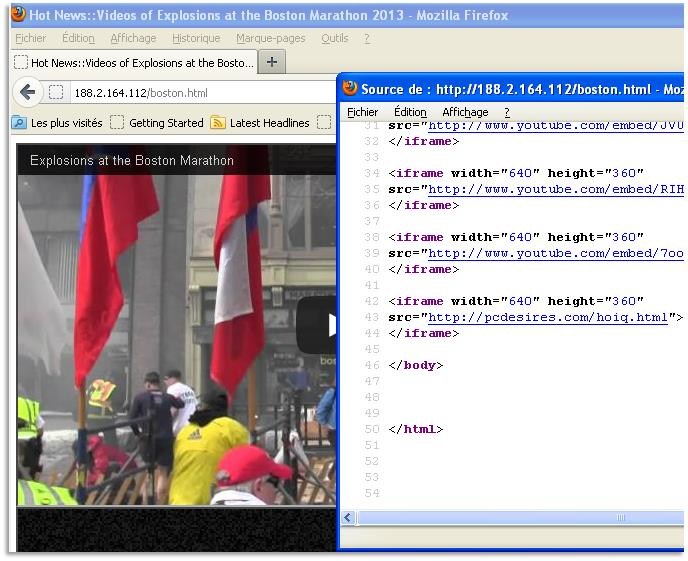
Victims who click the malicious link are directed to a page that loads several iframes. The iframes perform simultaneous actions when rendered in a victim’s web browser:

Figure 2. Video loaded by an iframe after clicking the link. Example of loaded iframes at right.
After the web browser loads the Redkit landing page, Redkit initiates a series of requests that ultimately lead to the installation of a variety of malware (see Figure 3).

Figure 3. Malicious request chain, starting from the original link contained within the spam. (Source: Dell SecureWorks)
The CTU research team has observed this spam campaign installing several malware families:
Figure 4 shows activity for these threats observed by the CTU research team between March 17 and April 17, 2013.
Figure 4. Alert activity for the past 30 days. (Source: Dell SecureWorks)
The CTU research team has developed the iSensor signatures/countermeasures in Table 1 to detect activity associated with this spam campaign. Third-party devices receive updated protection as it is released from the respective vendors and deployed by Dell SecureWorks device management security teams.
| Signature ID | Alert Message |
| 47934 | Redkit Returning AES Encrypted Payload |
| 48446 | Trojan Win32/Karagany.I Requesting Encoded EXE |
| 33390 | Pony Downloader Trojan Phone Home Request Detected |
| 47815 | ZeroAccess GeoIP check with Maxmind |
| 39204 | Waledac/Storm V4 Trojan Contacting Peer |
Table 1. Dell SecureWorks iSensor countermeasures covering this spam activity.
To mitigate exposure to these malware, CTU researchers recommend that customers use available controls to restrict access the indicators listed in Table 2.
| Indicator | Type | Context |
| hxxp:// 178.137.120.224/news . html | Web page | Web page that loads iframes to redirect to Redkit and YouTube. |
| hxxp:// 95.87.6.156/news . html | Web page | Web page that loads iframes to redirect to Redkit and YouTube. |
| hxxp:// 188.2.164.112/boston . html | Web page | Web page that loads iframes to redirect to Redkit and YouTube. |
| hxxp:// 178.137.120.224/news . html | Web page | Web page that loads iframes to redirect to Redkit and YouTube. |
| hxxp:// 46.233.4.113/boston . html | Web page | Web page that loads iframes to redirect to Redkit and YouTube. |
| hxxp:// 94.28.49.130/boston . html | Web page | Web page that loads iframes to redirect to Redkit and YouTube. |
Table 2. Indicators for this spam activity.