
Actually, this latest ransomware outbreak is not Petya. The malware appears to share a significant amount of code with an older piece of ransomware that really was called Petya, but after the outbreak started, security researchers noticed that “the superficial resemblance is only skin deep”.
Researchers at Russia’s Kaspersky Lab redubbed the malware NotPetya, and then folks played the name game and variation like Petna, Pneytna began to spread as a result. As if that didn’t complicate matters, other researchers gave it other names like Goldeneye (dubbed so by Bitdefender).
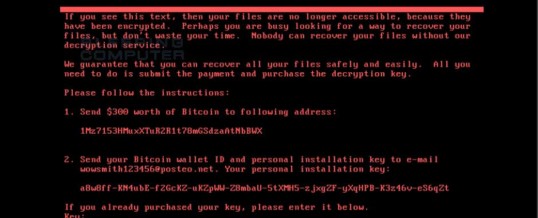
The ransomware takes over computers and demands $300, paid in Bitcoin. However, the mechanisms put in place to collect the ransom quickly fell apart (and we all know payment was never a real option anyway). The initial infection vector while not 100% confirmed it is currently speculated to have come from an Ukrainian software product called MeDoc which is believed to have been compromised. The malicious software spreads rapidly across an organization once a computer is infected using multiple techniques. The first was utilizing the EternalBlue exploit which leverages a Windows vulnerability (MS17-010) that has been previously fixed by Microsoft in March of this year. It then utilizes a stripped down version of Mimikatz and lsadump to extract clear-text credentials from the infected machine. These credentials in combination with a custom version of PSEXEC and WMIC is then how it move laterally and infects other mahcines on the network. “It has a better mechanism for spreading itself than WannaCry”, said Ryan Kalember, of cybersecurity company Proofpoint.
NotPetya attempts to capture credentials for spreading, the ransomware uses custom tools, a la Mimikatz. These tools extract credentials from the lsass.exe process. After extraction, credentials are passed to PsExec tools or WMIC for distribution inside a network.
Other observed infection vectors include:
Computers running the most recent update of Microsoft’s software should be safe from the attack. Users are advised to check they have installed the latest version of Windows and refrain from clicking on malicious links.
TBG Security advises our clients to never pay the ransom as it only encourages the attackers (and most times you’ll not get the files recovered anyway).
Instead, power off your machine, format your drive and restore from backup. We know it sounds harsh but the other option is to stay online and spread the ransomware throughout the network.
Patching makes Perfect. First, if you have not already patched your Windows machines and servers against the Microsoft vulnerability exploit (MS17-010), do it right now. Microsoft’s Windows Defender AV detects and removes this threat. as well.
To reduce the possibility of becoming infected with ANY ransomware infection, do not open uninvited emails, emails from people or businesses you do not recognize and NEVER click on any attachments unless you know what you are opening. And as a best practice you should always backup your files to some type of external device that is not connected to your PC or your network.
If you don’t have an AntiVirus software package running on your PC (what are you thinking) then install one ASAP and keep the definitions up to date. Most, if not all Av packages will automatically update the virus definitions but it’s up to you to set up an effective scanning solution.