
A serious vulnerability has been found in the Bash command shell, which is commonly used by most Linux distributions. This vulnerability – designated asCVE-2014-7169- allows an attacker to run commands on an affected system. In short, this allows for remote code execution on servers that run these Linux distributions
The most popular shell on *nix environments has a serious flaw which can allow an attacker to run any arbitrary command over the network where its used behind the curtains. The most common being web servers using CGI environment.
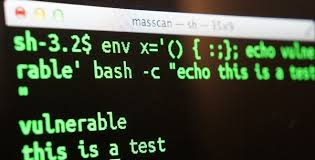
Bash allows exporting shell functions to other bash instances. It is done by creating an environment variable with the function definition. For example,
env ENV_VAR_FN=() { };
The ENV_VAR_FN will be the function that is exported to any subsequent bash instances. This seems like a useful feature, right? But there is a bug in the implementation of bash that it continues to read beyond the function definition and executes commands that follow the definition. In an ideal scenario, it should have stopped reading beyond the definition and ignored whatever came after it, but it doesn’t.
env ENV_VAR_FN=() { };
Given the fact that bash environment is used in several configurations including CGI, ssh, rsh, rlogin etc., all those services can be affected by this bug. Any web servers which consume user input and absorb them into bash environment are also vulnerable. Heres how a bad request would look like in a CGI environment:
GET / HTTP/1.1
User-agent: () { :;}; echo something>/var/www/html/new_file
And this will create a new file new_file for the attacker.
Web applications are the biggest exposure layer for this vulnerability. However, this can manifest itself via several other services as noted above.
The above just demonstrates creating a file but an attacker can literally run any command that’s conceivable on a bash shell. This could mean modifying the contents of the web server itself, change the website code, deface the website, steal user data from the databases, change permissions on the website, installing backdoors etc.
Remember that it will be run in the context of user running the web server. This is generally httpd user. Note that there is no elevation of privilege solely with this vulnerability, but it can be used in conjunction with another local vulnerability to escalate privileges to root user. It is not uncommon for attackers to cascade different exploits to gain entry into a system/network.
Shell scripting is widely used in Linux, which means there are multiple ways for this vulnerability to be triggered. Bash is used by most Unix and Linux systems, as well as OS X. Red Hat, one of the biggest companies that provides Linux, said in a bulletin to its customers that “Because of the pervasive use of the Bash shell, this issue is quite serious and should be treated as such.”
In addition, because Linux (and correspondingly, Bash) is used on many embedded Internet of Things/Internet of Everything (IoT/IoE) devices, the risk of devices with vulnerabilities and difficult-to-impossible to patch can’t be ruled out either. Lastly, there are news stating that Bitcoin/Bitcoin minining may also be affected by this security issue.
All versions of Bash up to and including version 4.3 are vulnerable. To be sure, check with your *nix vendor’s website for specific patched versions. Redhat customers can refer here.
The first thing is to upgrade the version of Bash to its latest version. Given the level of compromise, ensure the integrity of your web server is not compromised by replacing your ssh keys, since they could have been stolen. It is also best to change credentials and check your database logs to see any mass scraping queries are run.
Read the full story on trendmicro.com