

Earlier this month, TBG Security took part in the The Palmetto Cyber Defense Competition (PCDC).
PCDC is a three-day cyber defense competition created through the collaboration of two organizations: the Space and Naval Warfare Systems Center Atlantic (SPAWAR) and the South Carolina Lowcountry Chapter of the Armed Forces Communications and Electronics Association (AFCEA).
Designed to energize high school and college students about an exciting future in the cybersecurity industry, the event promotes the importance of cyber security education and awareness by gamifying the role and responsibilities of IT security administrators.
The Annual PCDC competition is made up of three categories.
The first category tests service up-time. Teams must ensure a list of services are available, mimicking real business needs.
The second category tests knowledge, asking participants to answer technical and security-related questions on topics such as network traffic analysis, reverse engineering, and/or log analysis.
For the third category, competitors are divided into two groups: Red team (attackers) and Blue team (defenders). PCDC creates a virtual business model to simulate business operations for the Blue team to manage. This year, the model was designed to mimic the delivery of medicine to area hospitals on a set schedule, as well as respond to email requests. The Red team attempts to infiltrate and disrupt the system, while the Blue team defends it.
On the final day of the competition, PCDC invited a hybrid team of six professionals, each representing a different company, to play the part of the Blue team.
The professionals had a representative from RSA, Adapt Forward, US-DGS, CACI, KSH and TBG Security. The team had a very broad and deep skill-set which seemed perfectly aligned with the task at hand.
There was a major drawback for the professional Blue team. While the attacking Red team had honed its knowledge of the target system over the previous two days, the professionals were denied access to the system prior to the kick-off of the professional day.
The Blue Team quickly decided to first check the systems, one by one, for command and control channels, and then change passwords in order to stop the Red Team from gaining access.
While the strategy was sound, the professional Blue team faced technical difficulties with the contest environment being entirely virtual, which introduced a significant lag time. Sadly, by the time the Blue team managed to access the system, the Red Team had already infiltrated it.
The Blue team now faced the slow and painful process of removing the Red Team from the network and ensuring services were back online.
Some techniques employed by the professional Blue team included:
To exploit Linux machines within the Blue team’s environment, the Red Team ran a script nicknamed “breaker.” This script identified and moved all vital binaries on the system, replacing them with empty files.
The breaker script deployed the Red Team’s SSH keys, changed the root password, and modified the attributes of the entire file system to render it immutable, removing Blue Team’s ability to make any changes.
Overcoming this setback proved to be one of the hardest challenges of the competition.
The Blue team was eventually able to defeat this attack by using local exploits on the system to regain root access, remove the chattr attributes, the ssh keys, and finally restore the binaries.
The image below shows the infiltrating traffic from the Red Team:
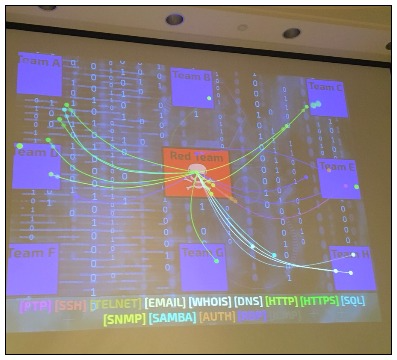
While the professional Blue team lost points with respect to service up time and had issues with the medical simulation, the team aced the knowledge component by being the only team competing to answer every single question correctly.
It was a gruelling fight, and while the Professional Blue team was unable to take away the gold medal, they ranked in the top three.
The Red team proved to be knowledgeable adversaries and deserve to be congratulated on their efforts.
A big thank you to PCDC for allowing TBG Security to compete this year. It was an engaging and exciting experience, and we even uncovered some new techniques and procedures which we can employ to defend our customers.
Next Year, TBG Security plans to send mentors to help the High School and College level teams, as well as playing in the professional day events.
TBG Security is a leading provider of information security and risk management solutions for Fortune 100 and Fortune 500 companies. TBG designs and delivers cyber security solutions to work in harmony with existing operations. Companies depend on TBG services in areas including risk management, penetration testing, security policy development, security strategies for compliance, business continuity, network security, managed services, software and service integration and incident response.
For more information on how TBG Security can help your organization with your information security initiatives please visit https://tbgsecurity.com.